Which Type Of Trojan Enables The Attacker To Upload, Download, Or Move Files On The Victim Machine?
What are the Types of Malware?
While there are many different variations of malware, y'all are near likely to run across the post-obit malware types:
| | | |
|---|---|---|
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
Below, we describe how they work and provide real-world examples of each.
1. Ransomware
Ransomware is software that uses encryption to disable a target'southward access to its information until a ransom is paid. The victim arrangement is rendered partially or totally unable to operate until it pays, just in that location is no guarantee that payment volition outcome in the necessary decryption key or that the decryption key provided volition part properly.
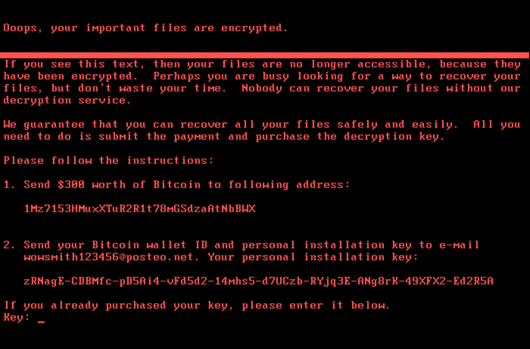
Instance of a ransom letter
Ransomware Example:
This year, the city of Baltimore was hit by a blazon of ransomware named RobbinHood, which halted all city activities, including revenue enhancement drove, property transfers, and regime e-mail for weeks. This set on has toll the metropolis more than $eighteen million so far, and costs continue to accrue. The same type of malware was used against the metropolis of Atlanta in 2018, resulting in costs of $17 million.
2. Fileless Malware
Fileless malware doesn't install annihilation initially, instead, it makes changes to files that are native to the operating system, such equally PowerShell or WMI. Considering the operating arrangement recognizes the edited files as legitimate, a fileless attack is not caught by antivirus software — and because these attacks are stealthy, they are upwards to 10 times more successful than traditional malware attacks.
Fileless Malware Case:
Astaroth is a fileless malware entrada that spammed users with links to a .LNK shortcut file. When users downloaded the file, a WMIC tool was launched, along with a number of other legitimate Windows tools. These tools downloaded additional lawmaking that was executed merely in memory, leaving no evidence that could be detected by vulnerability scanners. Then the attacker downloaded and ran a Trojan that stole credentials and uploaded them to a remote server.

Fileless Intrusions
Download our white paper to go a detailed anatomy of a fileless intrusion.
Download At present
iii. Spyware
Spyware collects data virtually users' activities without their knowledge or consent. This can include passwords, pins, payment information and unstructured letters.
The use of spyware is non limited to the desktop browser: it can besides operate in a critical app or on a mobile phone.
Even if the information stolen is non critical, the furnishings of spyware often ripple throughout the organization as performance is degraded and productivity eroded.
Spyware Example:
DarkHotel, which targeted business and regime leaders using hotel WIFI, used several types of malware in club to gain access to the systems belonging to specific powerful people. One time that access was gained, the attackers installed keyloggers to capture their targets passwords and other sensitive information.
iv. Adware
Adware tracks a user's surfing activeness to determine which ads to serve them. Although adware is similar to spyware, information technology does not install any software on a user's estimator, nor does it capture keystrokes.
The danger in adware is the erosion of a user's privacy — the data captured past adware is collated with data captured, overtly or covertly, well-nigh the user's activity elsewhere on the cyberspace and used to create a profile of that person which includes who their friends are, what they've purchased, where they've traveled, and more. That information tin be shared or sold to advertisers without the user'due south consent.
Adware Example:
Adware called Fireball infected 250 meg computers and devices in 2017, hijacking browsers to change default search engines and rails web activity. However, the malware had the potential to get more than a mere nuisance. Three-quarters of it was able to run lawmaking remotely and download malicious files.
Expert Tip
Download CrowdInspect: a free community tool for Microsoft Windows systems that is aimed to help alarm you to the presence of potential malware are on your computer that may be communicating over the network.Download CrowdInspect
v. Trojan
A Trojan disguises itself equally desirable code or software. In one case downloaded by unsuspecting users, the Trojan can take command of victims' systems for malicious purposes. Trojans may hide in games, apps, or even software patches, or they may exist embedded in attachments included in phishing emails.
Trojan Case:
Emotet is a sophisticated banking trojan that has been around since 2014. It is hard to fight Emotet because it evades signature-based detection, is persistent, and includes spreader modules that help it propagate. The trojan is so widespread that it is the subject field of a US Section of Homeland Security alert, which notes that Emotet has toll state, local, tribal and territorial governments up to $1 million per incident to remediate.
Learn More than
TrickBot malware is a type of cyberbanking Trojan released in 2016 that has since evolved into a modular, multi-phase malware capable of a wide variety of illicit operations. Learn more nigh what makes TrickBot highly concerning here.Read: What is TrickBot Malware
half-dozen. Worms
Worms target vulnerabilities in operating systems to install themselves into networks. They may proceeds access in several ways: through backdoors congenital into software, through unintentional software vulnerabilities, or through flash drives. Once in place, worms can exist used by malicious actors to launch DDoS attacks, steal sensitive data, or conduct ransomware attacks.
Worm Example:
Stuxnet was probably adult by the United states and Israeli intelligence forces with the intent of setting dorsum Islamic republic of iran'due south nuclear program. It was introduced into Iran'southward environs through a wink drive. Because the environs was air-gapped, its creators never thought Stuxnet would escape its target's network — but information technology did. Once in the wild, Stuxnet spread aggressively only did little damage, since its only office was to interfere with industrial controllers that managed the uranium enrichment process.
Learn More than
Want to stay up to engagement on contempo adversary activities? End by the Research and Threat Intel Blog for the latest research, trends, and insights on emerging cyber threats.Enquiry and Threat Intel Web log
vii. Virus
A virus is a piece of code that inserts itself into an awarding and executes when the app is run. In one case inside a network, a virus may be used to steal sensitive data, launch DDoS attacks or conduct ransomware attacks.
Viruses vs. Trojans
A virus cannot execute or reproduce unless the app it has infected is running. This dependence on a host application makes viruses unlike from trojans, which require users to download them, and worms, which do non use applications to execute. Many instances of malware fit into multiple categories: for instance, Stuxnet is a worm, a virus and a rootkit.
8. Rootkits
A rootkit is software that gives malicious actors remote command of a victim'south computer with full administrative privileges. Rootkits can be injected into applications, kernels, hypervisors, or firmware. They spread through phishing, malicious attachments, malicious downloads, and compromised shared drives. Rootkits can besides be used to muffle other malware, such equally keyloggers.
Rootkit Case:
Zacinlo infects systems when users download a fake VPN app. One time installed, Zacinlo conducts a security sweep for competing malware and tries to remove it. Then it opens invisible browsers and interacts with content like a human would — by scrolling, highlighting and clicking. This activity is meant to fool behavioral analysis software. Zacinlo's payload occurs when the malware clicks on ads in the invisible browsers. This advertising click fraud provides malicious actors with a cutting of the commission.
Larn More than
Web log Postal service on Machine Learning & Malware Defense: Acquire where automobile learning can be almost valuable and serve as an effective tool confronting both known and unknown malware. Read Web log
9. Keyloggers
A keylogger is a type of spyware that monitors user action. Keyloggers have legitimate uses; businesses tin can apply them to monitor employee activity and families may use them to keep track of children's online behaviors.
Even so, when installed for malicious purposes, keyloggers can be used to steal countersign data, cyberbanking information and other sensitive information. Keyloggers tin be inserted into a system through phishing, social engineering science or malicious downloads.
Keylogger Example:
A keylogger called Olympic Vision has been used to target Usa, Eye Eastern and Asian businessmen for business electronic mail compromise (BEC) attacks. Olympic Vision uses spear-phishing and social engineering techniques to infect its targets' systems in order to steal sensitive data and spy on business transactions. The keylogger is not sophisticated, simply information technology's available on the black market place for $25 so it's highly accessible to malicious actors.

2022 CrowdStrike Global Threat Report
Download the 2022 Global Threat Report to discover out how security teams can better protect the people, processes, and technologies of a modern enterprise in an increasingly ominous threat mural.
Download Now
ten. Bots/Botnets
A bot is a software application that performs automatic tasks on command. They're used for legitimate purposes, such equally indexing search engines, but when used for malicious purposes, they take the form of self-propagating malware that can connect back to a primal server.
Ordinarily, bots are used in large numbers to create a botnet, which is a network of bots used to launch broad remotely-controlled floods of attacks, such as DDoS attacks. Botnets can become quite expansive. For example, the Mirai IoT botnet ranged from 800,000 to 2.5M computers.
Botnet Case:
Echobot is a variant of the well-known Mirai. Echobot attacks a wide range of IoT devices, exploiting over l dissimilar vulnerabilities, simply it also includes exploits for Oracle WebLogic Server and VMWare's SD-Wan networking software. In improver, the malware looks for unpatched legacy systems. Echobot could be used by malicious actors to launch DDoS attacks, interrupt supply chains, steal sensitive supply concatenation information and acquit corporate sabotage.
11. Mobile Malware
Attacks targeting mobile devices have risen 50 percent since last year. Mobile malware threats are as diverse equally those targeting desktops and include Trojans, ransomware, advertising click fraud and more. They are distributed through phishing and malicious downloads and are a particular problem for jailbroken phones, which tend to lack the default protections that were part of those devices' original operating systems.
Mobile Malware Example:
Triada is a rooting Trojan that was injected into the supply chain when millions of Android devices shipped with the malware pre-installed. Triada gains access to sensitive areas in the operating system and installs spam apps. The spam apps display ads, sometimes replacing legitimate ads. When a user clicks on ane of the unauthorized ads, the revenue from that click goes to Triada's developers.

Mobile Threat Report
Download the latest mobile threat report to explore why the targeting of mobile platforms is being increasingly adopted
Download Study
Malware Detection and Removal with CrowdStrike
The best approach to protect against malware is to apply a unified assortment of methods. Machine learning, exploit blocking, whitelisting and blacklisting, and indicators of set on (IOCs) should all be part of every system's anti-malware strategy.
CrowdStrike Falcon combines these methods with innovative technologies that run in the deject for faster, more than up-to-the-minute defenses.
The CrowdStrike Falcon platform gives analysts and threat researchers rapid and comprehensive malware search capabilities through access to the largest and most active repository of threat events and artifacts in the industry. The repository contains a 300TB collection with over 400 million files and indexes over 2 trillion events each week.
All of this data is available for real-fourth dimension search — both metadata and binary content — made possible within seconds past patent-pending indexing technology.
Deep assay of evasive and unknown threats is a reality with Falcon Sandbox. Falcon Sandbox enriches malware search results with threat intelligence and delivers actionable IOCs, then security teams can better understand sophisticated malware attacks and strengthen their defenses.
To battle the growing threat of mobile malware, organizations need visibility into which devices are accessing their networks and how they're doing it. CrowdStrike's Falcon for Mobile delivers mobile endpoint detection and response with real-time visibility into IP addresses, device settings, WIFI and Bluetooth connections, and operating organization information.
Desire to see how the CrowdStrike Falcon Platform blocks malware? Start a free trial and see how it performs confronting live malware samples.
Get-go Gratuitous Trial
Source: https://www.crowdstrike.com/cybersecurity-101/malware/types-of-malware/
Posted by: gwinnonen1947.blogspot.com


0 Response to "Which Type Of Trojan Enables The Attacker To Upload, Download, Or Move Files On The Victim Machine?"
Post a Comment